Portfolio Projects
Throughout this cybersecurity course, you'll build the following real-world projects that demonstrate your security skills and methodology:
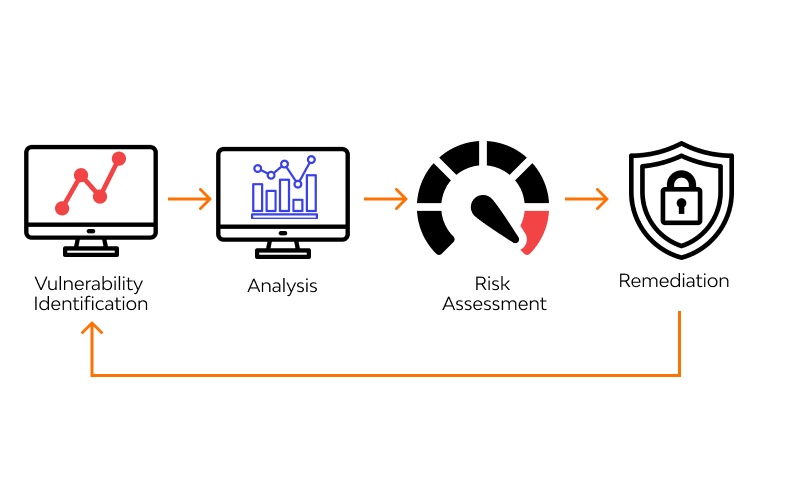
Security Assessment Report
Risk Assessment
Vulnerability Analysis
Security Frameworks
Documentation
Conduct a comprehensive security assessment of an organization and provide detailed findings and recommendations.
Network Security Implementation
Firewalls
IDS/IPS
Network Segmentation
Security Monitoring
Design and implement a secure network architecture with appropriate security controls and monitoring.
System Hardening Implementation
OS Hardening
Access Controls
Endpoint Protection
Security Baselines
Develop and implement system hardening procedures for Windows and Linux systems to reduce attack surface.
Penetration Testing Exercise
Ethical Hacking
Vulnerability Scanning
Exploitation
Security Reporting
Perform a controlled penetration test on a target environment, documenting methodology, findings, and remediation steps.
Secure Application Development
Secure Coding
OWASP
Security Testing
Code Review
Develop or modify an application with security built-in, implementing secure coding practices and security testing.
Incident Response Plan
Incident Response
Digital Forensics
SIEM
Security Operations
Create a comprehensive incident response plan including procedures, roles, and communication strategies.
Comprehensive Security Solution
Security Architecture
Risk Management
Cloud Security
Security Strategy
Design and document a complete security solution for an organization, addressing people, processes, and technology.